Metis: Α Cyber Threat Intelligence Workbench
Research, Manage and Operate on Threat Information

What is Metis?
The Networks and Information Systems Directive of the European Parliament and the Council of 6 July 2016 along with the National Institute of Standards and Technology have called for organizations to cooperate and exchange Cyber Threat Information Products (CTIPs) to counter cyber threats. The content and structure of CTIPs should adhere to a standardized format to enhance manageability and accessibility for both humans and machines. In the United States and the European Union, the Structured Threat Information eXpression (STIX) language is recognized as the standard for expressing CTIPs in a standardized and structured format.
Metis is a CTIP workbench that provides an intuitive and guided procedure to managing CTIPs throughout a life cycle, making it accessible even for those with limited expertise. Metis places a strong emphasis on standardization by conforming to STIX compliance, thereby ensuring uniformity and consistency. Finally, Metis prioritizes the enhancement of CTIP quality to improve overall cyber threat information management.
Main Features
Modeller (Producing Quality CTIPs)
Modeller offers an intuitive user interface, employing straightforward forms, to enable users to produce CTIPs. This module includes the following features:
- Reusability: Metis boosts productivity by supporting users to repurpose existing CTIPs, thus, eliminating the need to create new ones and preventing the platform from being cluttered with duplicates.
- CTIP Lifecycle: Employment of a specific lifecycle to ensure the quality of CTIPs, including the states of edit, draft and publish state.
- Auditing and Versioning: Metis supports monitoring development of CTIPs, offering versioning capabilities to pinpoint alterations to individual CTIPs over time, thereby enhancing transparency and historical tracking.
- Commenting: Usable user interface (UI) to provide feedback, or contribute additional information essential for enhancing management of CTIPs.
- Visualization: Visualized representation of CTIPs and their relationships, thereby improving comprehension and facilitating more effective CTIP production.
- Three-Tier Real-Time Validation: Metis incorporates a comprehensive three-tier validation of CTIP production against STIX, JSON schemas, and field-specific demands, that operates in real-time in order to prevent errors as soon as possible and ensure information accuracy and consistency.
- STIX Schema Management: Metis supports and guides users in editing and proposing new STIX schema versions and objects in the context of a collaborative development of the STIX schema.
Ingestor (Ingesting Data from Multiple Sources)
The Ingestor module allows for searching and importing external feeds (e.g. IoCs) provided by open sources (reports, social media, etc) in order to enable the enhancement of CTIPs with most up-to-date information. This module includes the following features:
- Source Credibility and Validity Classification: Metis categorizes open sources and their respective feeds by rating their trustworthiness based on their credibility and validity.
- CTIP Contextualized Filtering: Ingested CTIPs are filtered based on their context information (e.g., organization type, industry and location) that allows for more customized threat intelligence management.
- CTIP Correlation: Metis supports correlation of CTIPs originated from multiple sources to gain deeper insights and a more comprehensive understanding of potential threats.
Investigator (Investigating Risks and Threats)
The Investigator module maintains proper repositories wherein users can search for particular threats related to their organizations. This involves setting up search criteria, retrieving information from sources available through Metis, and then analyzing the data using common analytical techniques like network diagrams, scatterplots, word clouds, and more. Τhe produced intelligence can be disseminated to the respective stakeholders via multiple formats. This module includes the following features:
- Brand Protection Policies: Monitor your organization and your clients’ risk by receiving alerts for threats such as leaked credentials in the dark web, impersonating domains and profiles, and other exposed sensitive information.
- Threat Intelligence Reporting: Create investigations for specific Intelligence Requirements (IRs) according to the Intelligence Lifecycle, and produce high quality reports (i.e. Threat Assessments, Threat Actor Attribution, etc).
Exporter (Exporting of CTIPs to security tools)
The Exporter module offers the capability to export CTIPs to security tools, such as Microsoft Sentinel. This module involves the following:
- Platform Protection Alerting: It provides notifications and alerts for risks associated with the infrastructure operated within the organization. Additionally, it integrates with SIEM vendors to ensure that alerts can be received in the centralized alerting solution.
- CTIP Exporting: Integration with security tools, mostly SIEMs, to push CTIPs.
- CTI Reporting: It enables the production of high quality intelligence reports, in various formats.
Metis Area
The range of Metis applicability options is illustrated in the following diagram:
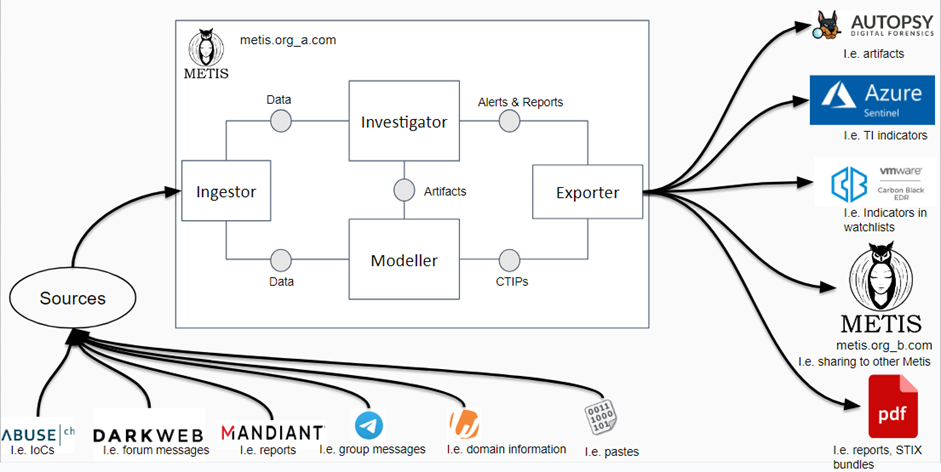
- Data from multiple sources are pulled by the Metis Ingestor module. These data can be of various types such as:
- IoCs from CTI feeds (e.g.., Abuse.ch, Phishtank, etc),
- forum messages and information from dark web locations (e.g., the Russian Marketplace, etc),
- CTI reports (e.g., from Mandiant, Crowdstrike, etc),
- Social media messages (e.g., from Telegram group chats, X tweets, etc),
- Domain information (e.g. from Whois, etc),
- Pastes (i.e. from Pastebin, etc)
- These data can then be inputted to the Modeller and Investigator modules.
- The Modeller module utilizes the collected data to assist the user in creating CTIPs. For example, a user can reuse IoCs from the URLHaus platform and produce a new Sighting object.
- The Investigator module utilizes the collected data, especially reports and data apart from IoCs, to assist the user in creating valuable reports based on the CTI Lifecycle (Direction, Collection, Analysis, Dissemination). For example a user creates and references reports from Mandiant for a specific APT and tweets from this APT; this enables for a more robust analysis and representation of evidence for a complete report. CTIPs can also be transferred as artifacts from Modeller to Investigator in order to refer to related IoCs for the APT group during the investigation.
- The Exporter module outputs the intelligence produced by the previous two modules, as follows:
- Modeller generates mainly CTIPs, which can then be inputted to multiple security tools, such as Autopsy (forensic artifacts), Microsoft Sentinel (TI indicators), VMWare Carbon Black (indicators in watchlists), as well as other Metis instances.
- Investigator generates intelligence in the form of reports and alerts:
- Reports: Created intelligence products inside Metis that referenced multiple data that were analyzed. The reports can be exported in multiple formats such as .pdf, .docx, .ppt, etc.
Use Cases
Managed Security Service Provider
- Use Case: A Managed Security Service Provider (MSSP) could utilize Metis for IoCs enrichment to improve detection capabilities and enhance the cybersecurity posture of its clients.
- How: Metis can ingest threat intelligence data from various sources via the Ingestor module, including IoCs, reports, and social media. MSSP analysts can utilize imported data and utilize the Metis’ searching techniques and CTIP correlation capabilities to enrich their clients’ existing IoCs with additional content and context. This enriched threat intelligence can then be integrated into the clients’ security systems, such as SIEMs and EDRs, to improve detection and response to cyber threats. Additionally, Metis’s platform protection features can help MSSPs to monitor for threats targeting their clients’ infrastructure and provide timely alerts.
Digital Forensic Examiners
- Use Case: Digital forensic examiners could use Metis for the purposes of conducting comprehensive investigations and gathering threat intelligence.
- How: During digital forensics investigations, examiners often need access to threat intelligence to understand the origin and nature of digital artifacts found on compromised systems. Metis allows examiners to search through a wealth of threat intelligence sources to gather context on IoCs discovered during investigations. It also offers the capability to create custom threat intelligence reports and IoCs specific to the case at hand. Moreover, Metis can facilitate the sharing of IoCs to digital forensics tools, aiding in the correlation of digital evidence and attribution of cyber incidents.
Small and Medium-Sized Companies
- Use Case: Small and medium-sized companies (SMEs) could use Metis for proactive threat monitoring and protection against emerging threats.
- How: SMEs often lack the resources and dedicated cybersecurity teams of larger organizations. Metis provides a solution for SMEs to ingest threat intelligence from various sources and receive alerts about threats relevant to their infrastructure. It can actively monitor for threats such as leaked credentials on the dark web, impersonating domains, or exposed credit card information. Metis enables SMEs to easily produce their own CTIPs when needed, and it can integrate with their existing security products to enhance overall protection without the need for a dedicated cybersecurity team.
Live Demo
The first version of Metis is now available online, and you can begin testing its functionalities.
To start using Metis, please follow these steps:
- Visit the following link https://shorturl.at/qxHW4.
- Click «Don’t have an account yet? Sign Up.»
- Provide a Login ID in the form to store in the platform as your username.
- Provide a strong password (complexity criteria are enabled) in the form’s fields of Password and Confirm Password.
- Click «Register».
- Once you have registered, enter the Login ID and Password you just created into the “Username” and “Password” fields, respectively.
- You are now ready to explore Metis and test its various features!